💻 개발 일지/SpringBoot
[SpringBoot/Kotlin] JWT + SpringSecurity를 활용한 회원 API 구현 (2) - JWT 로그인
점이
2023. 11. 12. 22:16
반응형
💡 본격적으로 JWT를 활용하여 로그인을 구현한다.
해당 장에서는 refreshToken 을 고려하지 않는다! (다음 장에서 구현 예정 ✅)
➡️ 1탄 바로가기: SpringSecurity 설정 및 회원가입
➡️ 3탄 바로가기: RefreshToken
CustomUser 생성
SpringSecurity에서 사용하는 `User` 클래스를 상속받아, 대체할 수 있는 `CustomUser` 클래스 생성
//CustomUser.kt
class CustomUser (
val id: UUID,
userName: String,
password: String,
authorities: Collection<GrantedAuthority>
): User(userName, password, authorities)CustomUserDetailsService
SpringSecurity에서 사용되는 `UserDetailsService` 가 `CustomUser` 를 사용하도록 서비스 생성
해당 서비스를 Bean으로 등록하게 되면, 스프링 시큐리티에서 자동으로 `UserDetailsService` 로 인식
➡️ SpringSecurity에서 제공하는 인증/인가를 사용할 때, CustomUserDetailService를 사용 (override한 메소드의 역할!)
➡️ 서비스에서 만든 CustomUser로 SpringSecurity의 인증/인가 처리 가능
@Service
class CustomUserDetailsService(
private val memberRepository: MemberRepository
): UserDetailsService {
override fun loadUserByUsername(username: String?): UserDetails =
memberRepository.findByEmail(username)
?.let { createUserDetails(it) } ?: throw UsernameNotFoundException("No User Info")
private fun createUserDetails(member: Member) : UserDetails =
CustomUser(
member.id!!,
member.email,
member.password,
listOf(SimpleGrantedAuthority("ROLE_${member.type}"))
)
}`loadUserByUsername()`
- username을 가진 User가 서비스 DB에 있는지 확인하는 메소드
- 구현한 `memberRepository`를 사용하여 User를 찾고, 해당 유저를 CustomUser로 컨버팅하여 Return
JWT Token Provider 생성
JWT 속성 정보
JWT 를 사용하는데에 필요한 속성 정보를 application.yml에 지정
-
해당 파일은 secretKey를 가지고 있으므로, 실 서비스의 경우 Github 및 외부에 노출되지 않도록 주의!
-
`secret` : JWT 토큰을 만드는데에 사용할 secret key 지정
- 영문 및 숫자 조합으로 32자 이상
- https://acte.ltd/utils/randomkeygen
jwt:
secret: AMmk3J4jybMhXbDqfvF8hg4e0MkloHUdToken Provider 생성
실제 토큰을 다루는 TokenProvider Component 생성: 토큰 생성, 유효성 검사 등을 수행한다.
CreateToken: 토큰 생성
@Component
class TokenProvider(
@Value("\${jwt.secret}") private val secret: String,
@Value("\${jwt.expiration-minutes}") private val expirationMinutes: Long
) {
private val key by lazy { Keys.hmacShaKeyFor(Decoders.BASE64.decode(secret)) }
/**
* 토큰 생성
*/
fun createAccessToken(authentication: Authentication): String {
val auth = authentication.authorities.joinToString(",", transform = GrantedAuthority::getAuthority)
val userId = (authentication.principal as CustomUser).id
return Jwts.builder()
.setIssuedAt(Timestamp.valueOf(LocalDateTime.now()))
.setExpiration(Date.from(Instant.now().plus(expirationMinutes, ChronoUnit.MINUTES)))
.setSubject(authentication.name)
.claim("auth", auth)
.claim("userId", userId)
.signWith(key, SignatureAlgorithm.HS256).compact()
}
}- `auth` : User의 권한들(`authorities`) 을 `,` 를 기준으로 스트링 생성 -> claim에 저장
- `userId`: CustomUser Id 즉, MemberId를 가져옴 -> claim에 저장
- JWT builder
-
`setIssuedAt`: 토큰 생성 시간
-
`setExpiration` : 토큰 만료 시간
- Refresh 토큰을 아직 구현하지 않았지만, 구현한다는 가정하에 30분으로 지정
-
`signWith`
- `key` : yml에 작성한 secretKey를 디코딩 하여 `HmacSHA` 키로 생성
- `signWith` : key와 알고리즘을 지정하여 JWT에 서명을 추가
-
GetAuthentication: 토큰 정보 추출
@Component
class TokenProvider(
...
) {
...
/**
* 토큰 정보 추출
*/
fun getAuthentication(token: String): Authentication {
val claims: Claims = getClaimsWithValidation(token)
return getAuthentication(claims)
}
// Claim 추출
private fun getClaimsWithValidation(token: String): Claims =
Jwts.parserBuilder().setSigningKey(key).build().parseClaimsJws(token).body
// Claim 내, Token 정보 추출
private fun getAuthentication(claims: Claims): Authentication {
val auth = claims["auth"] ?: throw RuntimeException("권한 정보가 없습니다.")
val userId = claims["userId"] ?: throw RuntimeException("권한 정보가 없습니다.")
val authorities: Collection<GrantedAuthority> = (auth as String).split(",").map { SimpleGrantedAuthority(it) }
val principal: UserDetails = CustomUser(UUID.fromString(userId.toString()), claims.subject, "", authorities)
return UsernamePasswordAuthenticationToken(principal, "", authorities)
}
}- `getClaimsWithValidation()` : `createToken` 시 넣어준 Claim 정보를 가져옴
- `parseClaimsJws()`: Token의 Validation도 같이 진행 -> Validation에 맞지 않을 경우 그에 맞는 Exception을 뱉음
- `ExpiredJwtException`, `UnsupportedJwtException`, `MalformedJwtException`, `SignatureException`, `IllegalArgumentException`
- `parseClaimsJws()`: Token의 Validation도 같이 진행 -> Validation에 맞지 않을 경우 그에 맞는 Exception을 뱉음
- `getAuthentication()` : Claim 속 정보 추출
- `auth`: 유저의 권한 리스트
- `userId`: CustomUser에 저장한 MemberId -> Member 스키마의 Key 값
-
최종적으로 `UserDetails` 와 권한 정보를 담은 `Authentication` 을 만들어 리턴
JwtAuthenticationFilter
매 요청마다 토큰을 검증할 Filter 생성
@Order(0)
@Component
class JwtAuthenticationFilter(
private val tokenProvider: TokenProvider
) : OncePerRequestFilter() {
override fun doFilterInternal(
request: HttpServletRequest, response: HttpServletResponse, filterChain: FilterChain
) {
resolveToken(request, TokenInfo.TokenType.ACCESS_TOKEN.value)?.let { token ->
handleAuthServlet(request, response) {
(tokenProvider.getAuthentication(token) to token)
}
}
filterChain.doFilter(request, response)
}
private fun resolveToken(request: HttpServletRequest, headerName: String): String? {
val bearerToken = request.getHeader(headerName)
return if (StringUtils.hasText(bearerToken) && bearerToken.startsWith(TokenInfo.TokenGrantType.BEARER.value)) {
bearerToken.substring(7)
} else null
}
private fun handleAuthServlet(
request: HttpServletRequest, response: HttpServletResponse, resolveAuthInfo:() -> Pair<Authentication, String>
) = try {
val (authentication, token) = resolveAuthInfo()
SecurityContextHolder.getContext().authentication = authentication
response.setHeader(TokenInfo.TokenType.ACCESS_TOKEN.value, token)
} catch (e: Exception) {
request.setAttribute("exception", e)
}
}- `resolveToken()`: `request`의 Header에 담긴 토큰을 가져온다.
- 해당 토큰의 GrantType(`Bearer`)을 제외하고 토큰만을 반환한다.
-
토큰이 있다면, `reolveToken` 을 진행하여 `authentication` 정보를 `SecurityContextHolder` 에 저장한다.
-
성공 시, Context 저장 및 response Header 저장
-
실패 시, request Attribute로 예외 저장
-
SecureConfig 필터 등록
이전 편에 생성했던 `SecureConfig > filterChain` 에 `JwtAuthenticationFilter` 를 등록
http
.httpBasic { it.disable() }
.csrf { it.disable() }
.sessionManagement { it.sessionCreationPolicy(SessionCreationPolicy.STATELESS) }
.authorizeHttpRequests {
it.requestMatchers("/auth/**", "/swagger-ui/**", "/v3/api-docs/**").permitAll()
.anyRequest().authenticated()
}
.addFilterBefore(
JwtAuthenticationFilter(tokenProvider),
UsernamePasswordAuthenticationFilter::class.java
)
.build()UsernamePasswordAuthenticationFilter(SpringSecurity 필터) 를 실행하기 전, 구현한 JwtAuthenticationFilter를 실행하도록 등록
Login 서비스 구현
Controller
data class TokenInfo(
val grantType: TokenGrantType = TokenGrantType.BEARER,
val accessToken: String
) {
enum class TokenGrantType(val value: String) {
BEARER("Bearer")
}
}@RequestMapping("/auth")
@RestController
class SignController(
private val signService: SignService
) {
...
@PostMapping("/sign-in")
fun login(@RequestBody signInRequest: SignInRequest): BaseResponse<TokenInfo> =
signService.signIn(signInRequest).let {
BaseResponse(data = it)
}
}accessToken을 담은 TokenInfo 객체를 Service로부터 받아 BaseResponse로 감싸 return 한다.
Service
@Transactional
@Service
class SignService(
...
private val authenticationManagerBuilder: AuthenticationManagerBuilder,
private val tokenProvider: TokenProvider
) {
...
@Transactional
fun signIn(signInRequest: SignInRequest): TokenInfo {
val authenticationToken = UsernamePasswordAuthenticationToken(signInRequest.email, signInRequest.password)
val authentication = authenticationManagerBuilder.`object`.authenticate(authenticationToken)
val accessToken = tokenProvider.createAccessToken(authentication)
return TokenInfo(accessToken = accessToken)
}
}- Controller로 받은 로그인 정보로 `UsernamePasswordAuthenticationToken` 생성
- `authenticate` : `CustomUserDetailsService` 의 `loadUserByUsername` 이 실행되어, 데이터베이스의 Member 정보와 일치하는지 비교
- 위 로직이 문제 없다면, 해당 authentication 정보로 `AccessToken` 을 생성하여 사용자에게 전달
Memberinfo 서비스 구현
MemberInfo 서비스는 Header에 있는 Access-Token을 가지고, 해당 회원의 정보를 반환하는 API
Controller
@RequestMapping("/member")
@RestController
class MemberController(
private val memberService: MemberService
) {
@GetMapping("/info")
fun getMyInfo(): BaseResponse<MemberInfoResponse> {
val userId = (SecurityContextHolder.getContext().authentication.principal as CustomUser).id
val userInfo = memberService.getInfo(userId)
return BaseResponse(data = userInfo)
}
}- `JwtAuthenticationFilter` 에서 저장한 인증 정보를 활용하여 `userId` 즉 MemberId를 가져옴
- 해당 MemberId를 가진 Member의 정보를 Service로부터 가져옴
Service
@Service
class MemberService(
private val memberRepository: MemberRepository
) {
fun getInfo(id: UUID): MemberInfoResponse {
val member = memberRepository.findByIdOrNull(id) ?: throw InvalidPropertiesFormatException("회원 정보가 없습니다.")
return member.toInfoDto()
}
}결과
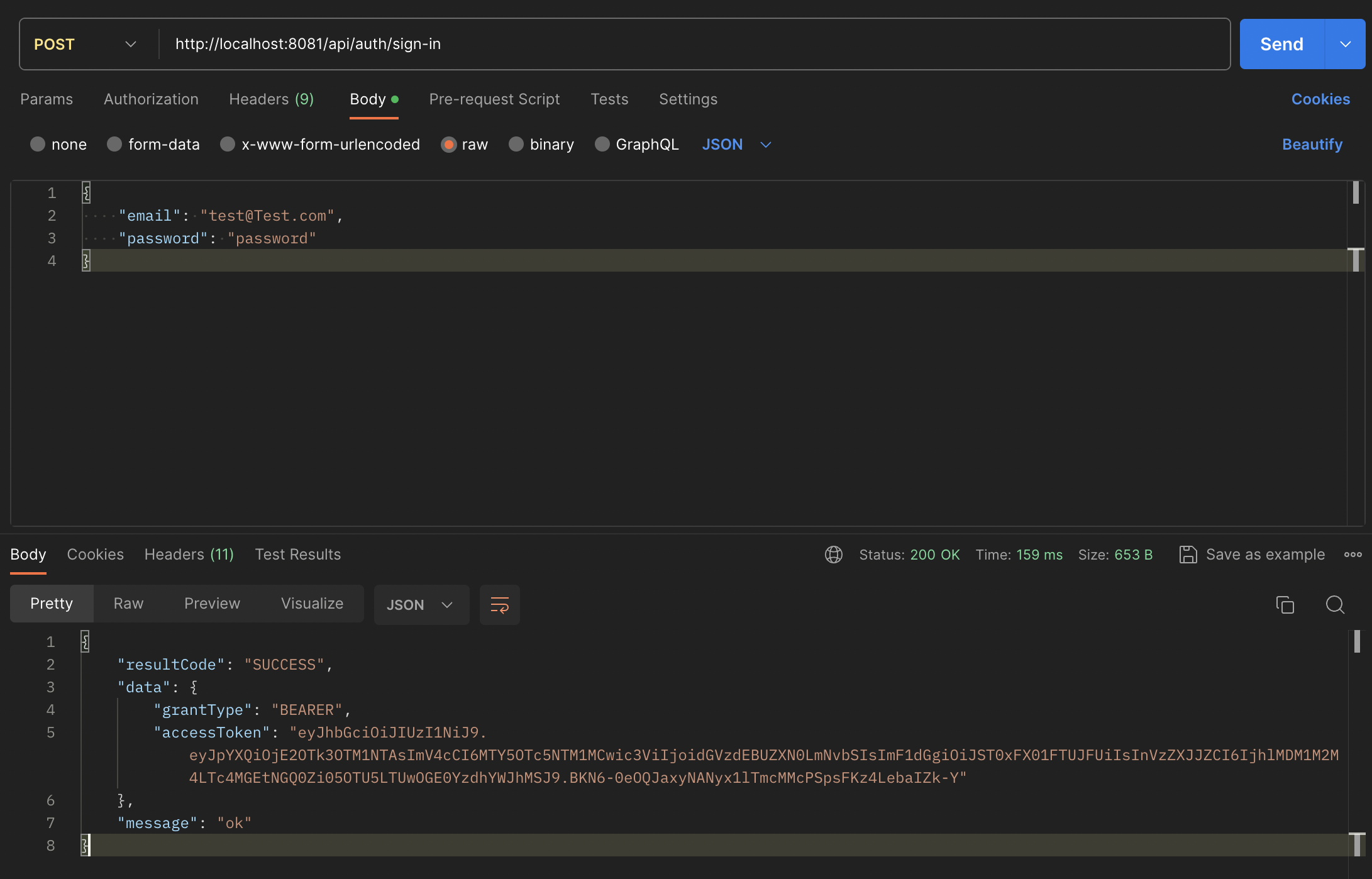
Login
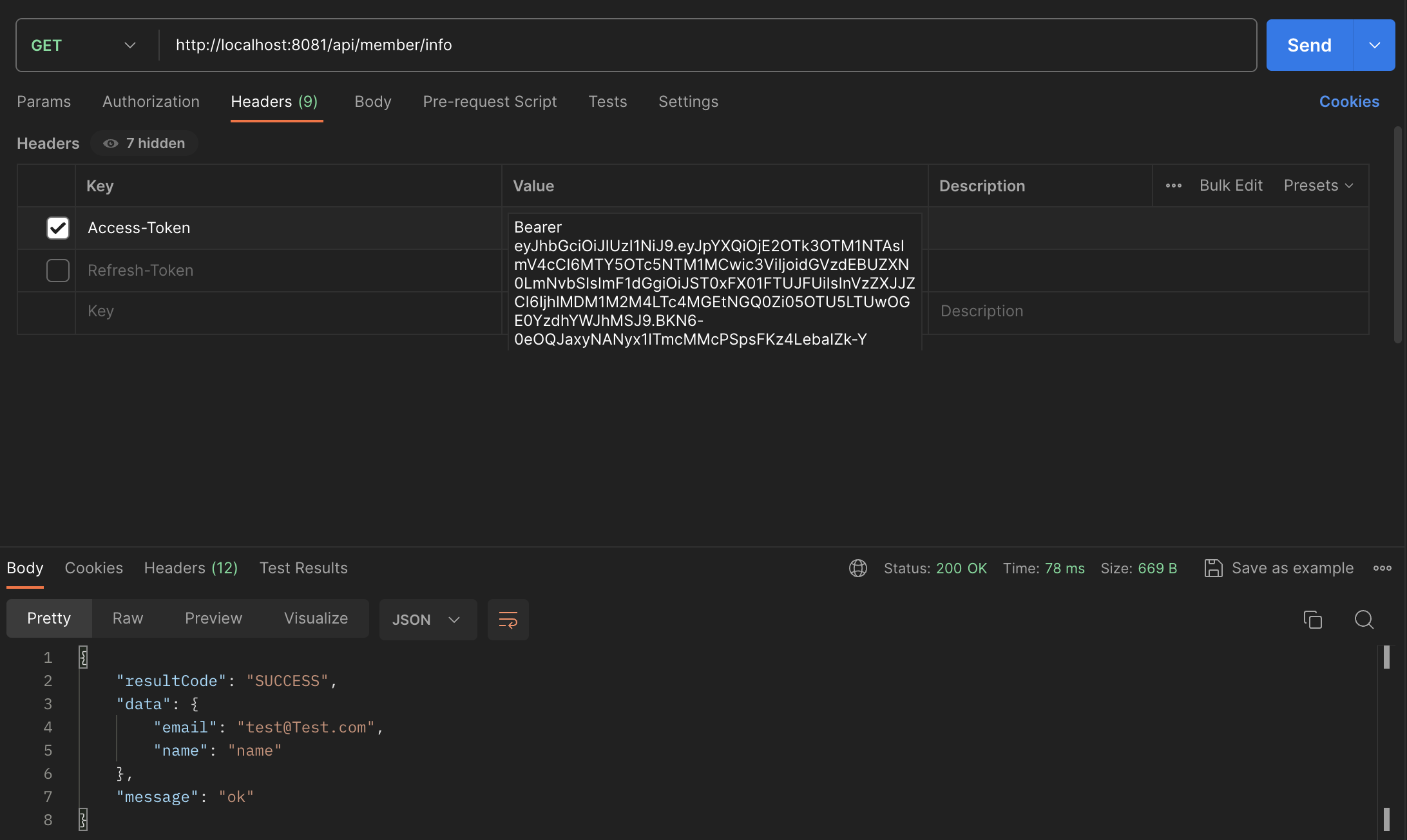
Member Info
위 로그인시에 받은 accessToken을 Header에 넣어 요청
✔️코드는 아래에서✔️
https://github.com/jeongum/spring-security-kotlin
GitHub - jeongum/spring-security-kotlin
Contribute to jeongum/spring-security-kotlin development by creating an account on GitHub.
github.com
반응형